Phishing as a defense
MokN Baits are defensive phishing pages that lure attackers into revealing compromised credentials before they’re used.
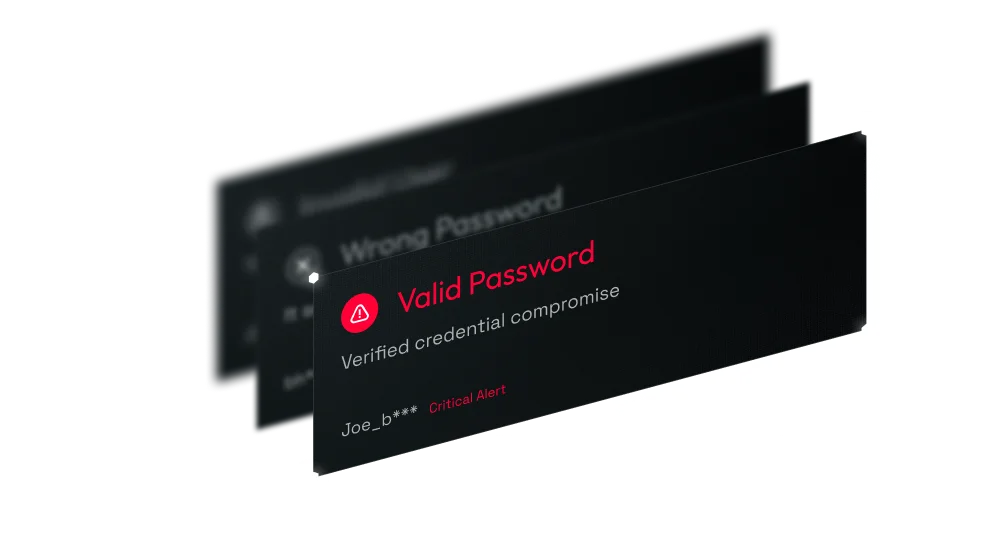
Only valid credentials
Millions of credentials may be tested. Our Baits filter the noise and alert only when valid ones are used against your systems.
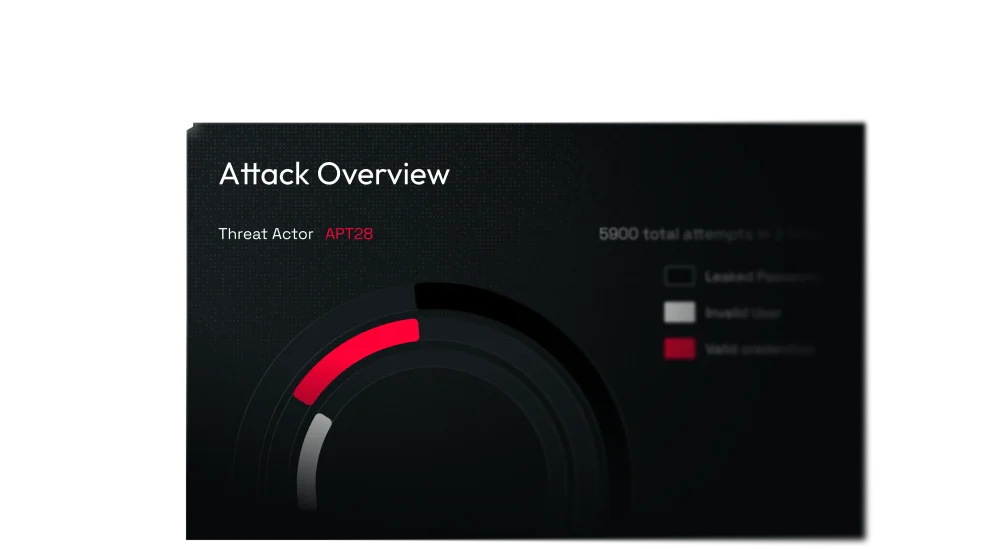
Tailored Threat intelligence
Monitor real attacker activity targeting your environment. No generic feeds, only insights tied to your users, systems, and domains.

Why MokN?
1B+
300+
960k+
Our customers
Don’t see any logos? That’s intentional.
We’ve chosen to keep our clients anonymous. But to give you a sense of scale, the combined annual revenue of organizations protected by MokN exceeds
We don’t showcase logos. We protect them.
Backed by strategic investors


Let’s meet at our next event
Meeting Mokn at the upcoming event promises to be a memorable experience. Get ready to exchange ideas and discover new perspectives. Don't miss this opportunity to connect with us!
Our next events:
Houston Cyber Peeps - Houston, USA / Feb 26, 2026
RSAC 2026 - San Francisco, USA / Mar 23-26, 2026
Still have questions? Let’s clear things up.
Here are answers to the most common questions we hear from security leaders exploring MokN.
Why hasn’t anyone done this before?
Because doing it right is hard.
Placing a decoy on the public internet means attackers have all the time in the world to inspect, fingerprint, and compare. If the setup doesn’t feel real, it gets ignored.
The second challenge is what happens when it doesn’t. Once a Bait is exposed, it faces constant traffic: scans, brute force, background noise. Extracting useful signals from that chaos is just as hard as building a convincing decoy.
We built Baits to solve both problems. Each instance is designed to replicate real services with extreme fidelity, and every alert is filtered and validated to remove false positives. The result is clean, confirmed signals tied to real credential misuse.
What sounds simple took years of research and iteration. But once you see it working, it makes perfect sense.
How do we know the concept works?
Because it already does. Across organizations of all sizes.
From 200-employee companies to multinational groups, Baits have consistently uncovered high-value signals:
- Freshly compromised credentials actively tested by attackers
- Breaches in progress that had gone unnoticed
- Insights into attacker tactics and targeting patterns
Every deployment confirms the value. No noise, no guesswork. Just confirmed signals your team can act on.
You can find concrete examples on our Baits.
How do we make sure attackers actually fall for the Baits?
Because we know how they think.
Our team comes from years of offensive security and pentesting. We understand how attackers explore an external perimeter, what catches their eye, and how they choose targets. That’s why every Bait is carefully contextualized to mimic your real assets, technologies, and domain naming conventions.
The result? High-fidelity traps that blend into your environment and naturally attract reconnaissance activity. No tricks, just realism.
How are Baits different from traditional honeypots?
Realism and relevance.
Internal honeypots catch attackers already inside. At that point, they’re rushing. They don’t have time to analyze what’s real or fake. That makes deception easier.
With Baits, it’s a different game. They’re exposed online, where attackers have time to probe, fingerprint, and compare. If something feels fake, they won’t bite. That’s why we invest serious effort in making Baits indistinguishable from your legitimate assets. Everything is designed for maximum credibility.
And since anything exposed online attracts noise, we’ve built logic to separate high-intent activity from random brute-force attempts. You only get clean, relevant signals.
Baits aren't passive traps. They're an active way to detect attackers before they reach your systems.
What’s the value if we already monitor the dark web?
Dark web monitoring often comes too late. Most stolen credentials are used long before they’re leaked or sold. Baits intercept compromised credentials at the source, as attackers actively test them. This gives your team time to neutralize the threat before it escalates.
We already have MFA. Do we really need this?
Yes. MFA reduces risk, but attackers increasingly find ways around it. Tactics like push fatigue, token theft, and social engineering can still give them access. Baits catches attackers in the act of using stolen credentials, regardless of your MFA setup. It provides a safety net when MFA is bypassed or disabled.